Traditional vs. Cloud Firewalls: What are the Key Differences?

In the modern digital society, the security of data and networks is more important than ever. Advanced cyber threats are encountered by businesses on a daily basis. Firewalls still serve as a major defense mechanism against them. However, the choice between a cloud firewall and a traditional firewall can often confuse decision makers. They both […]
UTM Firewall vs Traditional Firewall: Why It’s Smarter to Buy a UTM Today
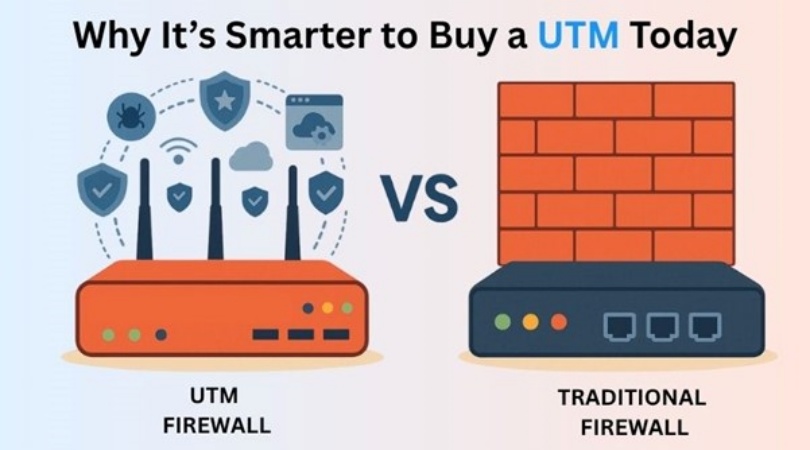
In today’s highly digital world, cyber threats have become a major issue. Simply filtering data packets is not sufficient; the businesses require an intelligent and combined one-stop protection system. That is exactly where Unified Threat Management (UTM) firewall excels over a traditional firewall. So why is it smarter to choose a UTM nowadays when it […]
UTM Appliances and Streamlining Your Network’s Cyber Security

Organizations face endless cyber-attacks these days that can compromise crucial information, bring operations to a standstill, and ruin reputations. Threats keep growing day by day, and traditional security systems tend to become ineffective. The Unified Threat Management solutions are very effective for the general security of the network. They combine multiple protective features into one […]
Fortinet Collaborates with Global Leaders at World Economic Forum Annual Meeting 2025

In January 2025, Fortinet, a leading firewall provider, marked its presence at the World Economic Forum meeting in Davos, Switzerland, which is held annually. It was the gathering of influential people from the business, government, and technology sectors to discuss the issues the world is facing today. Strategic Alliances and Joint Efforts Fortinet’s attendance at […]
How to automate rule management for AWS Network Firewall?

Data and resource security are important in a cloud-centric environment. AWS Network Firewall is an essential managed service that strengthens Virtual Private Cloud settings. It allows users to create and maintain rules that control the flow of traffic. However, the complications of rule administration can become a task, especially when the infrastructure requirements are growing. […]
Top 5 Cloud-Based Firewalls: Flexible and Scalable Security

We have all heard about the term firewall; it protects a network from unknown threats. But these days, with the evolution of technology, firewalls have become more advanced. Earlier, traditional firewalls were used, which did not have the capability to secure the network efficiently, but now, with the help of a next-generation firewall, the cyberthreats […]
Switches vs. router vs. firewall – difference and comparison
You are accustomed to an integrated device that “does it all” if you have experience with home networking equipment. You can have a single box that serves as your cable/DSL modem, router, firewall, switch, and wireless access point on your home network. Today, how many functions can fit inside just one box is astonishing. Some […]
How managed Firewall Services Help Boost Network Security

Innovative businesses have known for a long time that their digital and business processes are dependent on the data they store and the applications they use. Any organization’s very survival may be in jeopardy if the security, integrity, and accessibility of this vital data are not carefully maintained. The first line of protection against cyberattacks […]
How should security and networking groups manage the firewall?

The first step in managing and protecting your network from malicious actors is to create a well-thought-out strategic plan. Today, the goal of every business’s security strategy is to continuously protect the network from attacks that can jeopardize the success or reputation of its business. Organizations that use the internet for email, web applications, or […]
What are the Significance and Role of Firewall Logs

Firewalls are included in any organization’s defense-in-depth strategy. They effectively play a crucial part in guarding the network against unwanted intruders. A firewall keeps track of all traffic entering and leaving the network and guards against malicious activity. It is a network security method that keeps track of both inbound and outbound traffic using some […]

